Are you confused by SOAR vs SIEM? Don’t be! SecondCyber is providing you with this guide which dives into both explaining how SIEM detects threats and how SOAR automates responses, these are both security tools. We will guide you on how to leverage them together for powerful cybersecurity. SOAR (security orchestration, automation, and response) and SIEM (security information and event management) are critical cybersecurity solutions specialized for certain purposes.
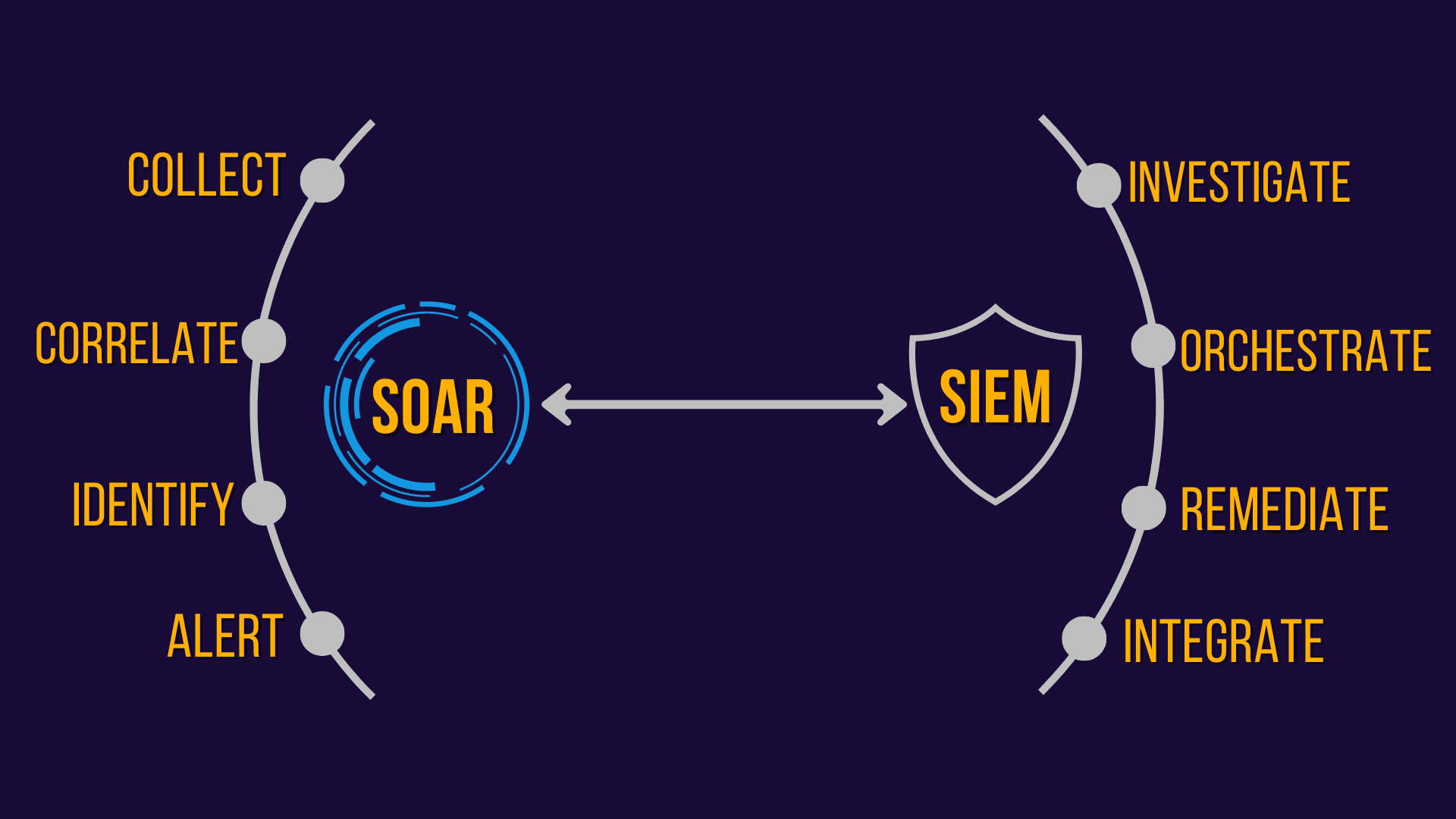
SOAR automates and coordinates security incident response, decreasing the workload on security professionals. It is useful for tackling repetitive chores, freeing analysts to concentrate on complex threats. SIEM, on the other hand, combines security information management (SIM) and security event management (SEM) in a single solution.
It collects and analyzes security data from many sources to detect and respond to security incidents that happen in real-time. While SIEM primarily collects and analyses security event data, SOAR enhances these capabilities with automation, orchestration, and predetermined incident response playbooks.
Difference Between SOAR & SIEM
SOAR and SIEM differ significantly in their functions and capabilities. These distinctions are critical in understanding how each tool contributes to a comprehensive security strategy.
Focus and Purpose
- SOAR platforms are primarily focused on automating and organizing incident response processes, enabling security teams to respond quickly and efficiently to security experiences and threats.
- SIEM systems are designed to collect, correlate, and analyze security event data from many sources to provide insights into potential security vulnerabilities, but with differing levels of automation for incident response.
Automation:
- SOAR solutions have broad automation capabilities, allowing for the execution of specified actions and workflows in response to security events or incidents. This automation shortens manual involvement and response time.
- SIEM systems enable varying levels of automation for incident response. They put more emphasis on data consolidation, correlation, and reporting.
Integration:
- SOAR platforms are well-known for their ability to connect with a wide range of security tools and technologies, enabling smooth communication and orchestration among various security solutions.
- SIEM solutions often integrate with several data sources to gather and centralize security event data, but they may provide a varying level of integration for automated incident response tasks.
Incident Response:
- SOAR platforms excel at incident response by providing a war room for investigation and communication, automating repetitive processes, orchestrating incident workflows, and allowing security teams to respond quickly to issues, lowering the mean time to resolution (MTTR).
- SIEM systems monitor security events and can produce alerts. However, they rely on human analysts to investigate, assess, and respond to issues, which might result in longer response times.
Manageability
- SOAR solutions are manageable and adaptable to a variety of security situations, allowing them to fit organizations of all sizes.
- SIEM solutions can be resource-intensive, requiring significant hardware and software infrastructure for bigger organizations.
What are the Benefits of SIEM?
Organizations that are looking to strengthen their cybersecurity defenses should take advantage of what SIEM systems offer.
Improved Security Monitoring via Data Collection and Analysis
SIEM technologies help monitor network traffic and security events. They gain information from different sources, which allows early detection of potential security problems. SIEM enables sudden threat identification and response by giving security professionals real-time visibility.
Improved Incident Response Times
SIEM solutions collect and correlate data from many sources, allowing for real-time detection and prioritization of security problems. This real-time alerting technique enables security experts to act quickly, minimizing potential damage and lowering threat response times.
Compliance Adherence
SIEM systems play a critical role in meeting regulatory standards. SIEM helps to discover and prioritize security problems by collecting and correlating various logs and events, decreasing response times, and mitigating potential damage.
Operational Efficiency
SIEM products include automation features that simplify operations like log aggregation, correlation, and alerting. This operational efficiency allows security analysts to concentrate on higher-level security issues and crucial responsibilities. Timely identification and reaction to security issues reduce the effect of breaches, lowering potential downtime and decreasing the risks associated with data breaches or system hacks.
Integration with other security solutions
SIEM solutions are known for their smooth integration with different security solutions such as intrusion detection systems, firewalls, and antivirus software. This integration provides organizations with a full view of their security environment. With this comprehensive picture, security teams may better understand patterns, discover vulnerabilities, and improve overall security strategy.
Also Checkout: 7 Best Virtualization Software in 2024
What are the Benefits of Soar?
SOAR systems are an important component of effective and efficient security operations. They have many benefits, making them a valuable instrument in the cybersecurity arsenal.
Increased SOC efficiency
One of the most notable benefits of SOAR is its ability to automate incident response operations. SOAR allows security analysts to focus on major occurrences by automating repetitive activities and integrating many security tools. SOAR provides preconfigured playbooks for a variety of use cases, including indication enrichment, alert deduplication, phishing, and ransomware response, threat intelligence feed management, malware investigations, and IT operations duties such as staff onboarding and offboarding.
Responds to incidents quickly
SOAR’s design emphasizes efficiency. It streamlines security procedures, links different security solutions, and strikes a balance between machine-driven security automation and human intervention. This strategy enables organizations to carry out security activities and incident responses efficiently, even at scale.
Ingest, Search, and Queries All Security Alerts
Complex, real-time investigations sometimes necessitate human assistance. SOAR guarantees that analysts have immediate access to search, query, and investigation capabilities, allowing them to respond to incidents faster. SOAR enables security teams to respond quickly and efficiently to evolving threats by bringing together alerts, incidents, and indications from any source on a single platform.
Facilitates analyst collaboration on investigations
SOAR’s collaborative investigative features encourage security analysts to work together. Analysts may support one another, perform real-time security commands, and learn from each occurrence by automatically documenting all actions.
Acts on threat intelligence
SOAR’s playbook-driven automation allows for the seamless unification, aggregation, scoring, and sharing of threat intelligence. Some SOAR solutions have built-in, high-fidelity threat intelligence, which can be enhanced by adding third-party threat intelligence feeds. This technique enables organizations to identify and prioritize important threats with greater agility and confidence.
Understanding the distinctions and benefits of SOAR and SIEM enables cybersecurity professionals, such as security analysts, SOC managers, and CISOs, to make informed decisions to improve their organization’s security posture. The combination of these tools creates a strong cybersecurity approach for efficiently detecting, responding to, and mitigating developing threats in today’s complex threat landscape.
Conclusion
In conclusion, the comparison of SOAR (Security Orchestration, Automation, and Response) and SIEM (Security Information and Event Management) shows the constantly changing nature of cybersecurity operations. While SIEM systems provide essential tools for real-time monitoring and detection of threats, SOAR platforms improve these capabilities by automating response actions and coordinating procedures, hence increasing operational efficiency and reducing response times to security incidents.
Finally, the decision between SOAR and SIEM is based on organizational requirements, resources, and the complexity of the cybersecurity threats encountered. Integrating both systems may provide a comprehensive cybersecurity defense strategy, providing proactive threat management and effective incident response in an increasingly linked digital world.
FAQs
What is the main difference between SOAR and SIEM?
SOAR focuses on automating and orchestrating incident response processes, whereas SIEM collects and analyzes security event data to detect threats in real time.
How do SOAR and SIEM work together in a cybersecurity strategy?
SIEM collects and analyzes data to detect potential threats, and SOAR uses this data to automate and coordinate incident responses, enhancing overall security efficiency.
Can SOAR and SIEM be used independently?
Yes, they can be used independently, but integrating them provides a more robust and comprehensive cybersecurity solution.
What are the benefits of using SIEM?
Benefits include improved security monitoring, faster incident response times, compliance adherence, operational efficiency, and seamless integration with other security tools.
What are the benefits of using SOAR?
Benefits include increased SOC efficiency, quick incident response, enhanced search and query capabilities, improved analyst collaboration, and effective threat intelligence utilization.
What types of tasks can SOAR automate?
SOAR can automate tasks like incident response playbooks, alert deduplication, threat intelligence management, and IT operations such as staff onboarding and offboarding.
How does SIEM improve operational efficiency?
SIEM automates log aggregation, correlation, and alerting, allowing security analysts to focus on more complex security issues and reducing the impact of breaches.
What should organizations consider when choosing between SOAR and SIEM?
Considerations include organizational requirements, available resources, the complexity of cybersecurity threats, and the need for automation and integration in their security operations.
How do SOAR’s collaborative features benefit security teams?
SOAR’s collaborative features enable security analysts to work together, share insights, perform real-time security commands, and document actions automatically, enhancing team efficiency.
Why is it important to integrate threat intelligence with SOAR?
Integrating threat intelligence with SOAR allows for better identification, prioritization, and response to significant threats, providing a more agile and confident security posture.